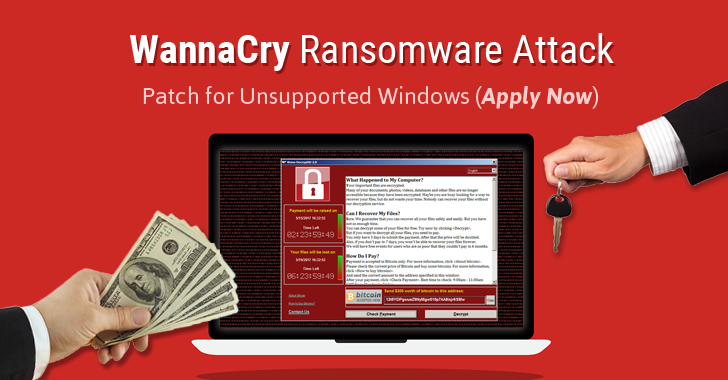
Friday’s ransomware outbreak, which used recently revealed weaknesses in Microsoft’s Windows operating system to spread further and faster than any before, has prompted the Redmond-based developer to break its own rules on software maintenance in an effort to keep users safe.
The ransomware, also known as “WanaCrypt0r”, “WeCry”, “WanaCrypt” or “WeCrypt0r”, used a vulnerability in a Windows Server component to spread within corporate networks. The weakness was first revealed to the world as part of a massive dump of software vulnerabilities discovered by the NSA and then stolen by a group of hackers calling themselves “Shadow Brokers”.

Microsoft fixed the flaw shortly before the stolen data was published, leading many to conclude it had been surreptitiously tipped-off by the security agency about the existence of the flaw.
But Microsoft’s policy is that some commonly used versions of Windows no longer receive security patches; those versions include Windows Server 2003 and Windows XP, both of which have not been sold for over a decade; and Windows 8, which some users prefer to the supported Windows 8.1 because of differences between the two versions of the operating system. Typically, the company only provides support to organisations which pay expensive fees for “custom support” for these out-of-date platforms.
May 05, 2014 Windows Server 2012 R2 Update is a cumulative set of security updates, critical updates and updates. Windows Server 2012 R2 Update is a cumulative set of security updates, critical updates and updates. Skip to main content. Download Center. Download Center. Download Center Home. Users can download and find more information about the patches in Microsoft’s blog post about Friday’s attack from the WannaCry ransomware. [ Further reading: The best antivirus for Windows PCs ].
Once WeCry began spreading, however, Microsoft took the “highly unusual” step of releasing free security updates for those out-of-support versions of Windows, which can be downloaded from its website.
How to defend against the ransomware
- The vulnerability does not exist within Windows 10, the latest version of the software, but is present in all versions of Windows prior to that, dating back to Windows XP.
- As a result of Microsoft’s first patch, users of Windows Vista, Windows 7, and Windows 8.1 can easily protect themselves against the main route of infection by running Windows Update on their systems. In fact, fully updated systems were largely protected from WanaCrypt0r even before Friday, with many of those infected having chosen to delay installing the security updates.
- Users of Windows XP, Windows Server 2003 and Windows 8 can defend against the ransomware by downloading the new patch from Windows.
- All users can further protect themselves by being wary of malicious email attachments, another major way through which the ransomware was spread.
A of Microsoft’s security response team, Phillip Misner, wrote: “We know that some of our customers are running versions of Windows that no longer receive mainstream support.
Windows Server 2003 Wannacry Patch
“That means those customers will not have received the … Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download.”
Although the malware’s main infection vector was through the vulnerability in Windows, it also spread in other ways which require changes in user behaviour to protect against. Phishing attacks with malicious attachments are the main way the malware ends up on corporate networks, meaning that users should be wary of opening such attachments if they seem unusual, as well as keeping all Microsoft Office applications up to date.
More and more antivirus platforms, including Microsoft’s own Windows Defender, are now recognising and blocking the malware, but relying on a purely technical fix means that a new variant of the software could sneak past the defences. Variations of the malware have already been seen in the wild, but they have lacked the capacity to spread themselves, which has vastly limited their proliferation.
For those who have been infected, paying the ransom may seem a tempting way out of trouble. But experts recommend against doing so, arguing that not only does it not guarantee restoration of any files, but it also funds future crime. And, for now, it appears that victims agree: fewer than 100 have actually paid up.
- What is ‘WanaCrypt0r 2.0’ ransomware and why is it attacking global computers?
(WannaCrypt Cyber-attack, Patch, Microsoft Updates & Best Practices)
WannaCrypt (WannaCry or .wncry)
Summary of immediate action items

Windows
- In March, Microsoft released a security update which addresses the vulnerability that these attacks are exploiting. Those who have Windows Update enabled are protected against attacks on this vulnerability. For those organizations who have not yet applied the security update, we suggest you immediately deploy Microsoft Security Bulletin MS17-010.
It's advisable to be proactive with security updates - To view all such from Microsoft:
https://technet.microsoft.com/en-us/security/bulletins - For customers using Windows Defender, we released an update, on 12 May 2017, which detects this threat as Ransom:Win32/WannaCrypt. As an additional 'defense-in-depth' measure, keep up-to-date anti-malware software installed on your machines. Customers running anti-malware software from any number of security companies can confirm with their provider, that they are protected.
- This attack type may evolve over time, so any additional defense-in-depth strategies will provide additional protections. (For example, to further protect against SMBv1 attacks, customers should consider blocking legacy protocols on their networks).
- Download English language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86,
Windows XP SP2 x64, Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86,
Windows 8 x64 - Download localized language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86, Windows XP SP2 x64, Windows XP SP3 x86, Windows XP Embedded SP3 x86, Windows 8 x86, Windows 8 x64
- MS17-010 Security Update: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- Download English language security updates: Windows Server 2003 SP2 x64, Windows Server 2003 SP2 x86,
Azure
- WannaCrypt attacks: guidance for Azure customers
What does this ransomware do?
Summary of long-term action items
You should:
- Install and use an up-to-date antivirus solution (such as Microsoft Security Essentials).
- Make sure your software is up-to-date.
- Avoid clicking on links or opening attachments or emails from people you don't know or companies you don't do business with.
- Ensure you have smart screen (in Internet Explorer) turned on.
- Have a pop-up blocker running in your web browser.
- Regularly backup your important files.
You can back-up your files with a cloud storage service that keeps a history or archive of your files, such as OneDrive which is now fully integrated into Windows 10 and Windows 8.1, and Microsoft Office.
After you've removed the ransomware infection from your computer, you can restore previous, unencrypted versions of your Office files using 'version history'.
For more tips on preventing malware infections, including ransomware infections, see: Help prevent malware infection on your PC.
Summary of tools from Microsoft, That Can Help
Windows 10: It is not vulnerable to this attack. (Hard target with security enabled)
Secure Productive Enterprise:
https://www.microsoft.com/en-IN/secure-productive-enterprise
Wannacry Microsoft Patch Windows 7
- Windows Update
- Windows Server Update Services (WSUS)
- System Center Configuration Manager (SCCM)
- Microsoft Intune
- Operations Management Suite – Update Management
- Windows Update
- Antimalware
- Windows Defender
- System Center Endpoint Protection (SCEP)
- Windows Defender
- Windows Backup (Available in all versions of Windows)
- Azure Backup
- System Center Data Protection Manager
- Windows Backup (Available in all versions of Windows)
- Threat Detection, Protection and Response
- Office 365 Advanced Threat Protection – SPE E5
- Windows Defender Advanced Threat Protection – SPE E5
- Operations Management Suite – Security and Audit
- Advanced Threat Analytics
- Microsoft Safety Scanner
- Office 365 Advanced Threat Protection – SPE E5
Trojan: Adylkuzz Microsoft Malware Protection Center has already released guidance towards this trojan. (Adylkuzz.A, Adylkuzz.B) - Updated systems will not be vulnerable. Adylkuzz can perform several actions of a malicious hacker's choice on your PC. Find out ways that malware can get on your PC. (The above advisory for WannaCry, is also applicable for Adylkuzz) Use the following free Microsoft software to detect and remove this threat:
You should also run a full scan. A full scan might find other hidden malware. You can also see our advanced troubleshooting page for more help.
|
Original Advisory This is an excerpt from the article 'Customer Guidance for WannaCrypt attacks' by MSRC Team as on May 12, 2017 Today many of our customers around the world and the critical systems they depend on were victims of malicious 'WannaCrypt' software. Seeing businesses and individuals affected by cyberattacks, such as the ones reported today, was painful. Microsoft worked throughout the day to ensure we understood the attack and were taking all possible actions to protect our customers. This blog spells out the steps every individual and business should take to stay protected. Additionally, we are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003. Customers running Windows 10 were not targeted by the attack today. Details are below.
We also know that some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the above mentioned Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download (see links below). Customers who are running supported versions of the operating system (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, Windows Server 2012 R2, Windows Server 2016) will have received the security update MS17-010 in March. If customers have automatic updates enabled or have installed the update, they are protected. For other customers, we encourage them to install the update as soon as possible. This decision was made based on an assessment of this situation, with the principle of protecting our customer ecosystem overall, firmly in mind. Some of the observed attacks use common phishing tactics including malicious attachments. Customers should use vigilance when opening documents from untrusted or unknown sources. For Office 365 customers we are continually monitoring and updating to protect against these kinds of threats including Ransom:Win32/WannaCrypt. More information on the malware itself is available from the Microsoft Malware Protection Center on the Windows Security blog. For those new to the Microsoft Malware Protection Center, this is a technical discussion focused on providing the IT Security Professional with information to help further protect systems. Further resources:
|
Frequently Asked Questions This is an excerpt from the article 'Ransomware' by Malware Protection Center What does ransomware do? There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC. They can target any PC users, whether it's a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider. Ransomware can:
Ransomware will demand that you pay money (a 'ransom') to get access to your PC or files. We have also seen them make you complete surveys. There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again. Frequently asked questions Is it true that the legal authorities in my area have detected illegal activities in my PC? No. These warnings are fake and have no association with legitimate authorities. The message uses images and logos of legal institutions to make the it look authentic. I cannot access my PC or my files. Should I just go ahead and pay to regain access? There is no one-size-fits-all response if you have been victimized by ransomware. There is no guarantee that handing over the ransom will give you access to your files again. Paying the ransom could also make you a target for more malware. How do I get my files back? How to recover your files depends on where your files are stored and what version of Windows you are using. Before you try to recover files, you should use Windows Defender Offline to fully clean your PC. For Microsoft Office files stored, synced, or backed up to OneDrive
For files on your PC
If you've been infected by the Crilock family of ransomware (also called CryptoLocker), you might be able to use the tool mentioned in the MMPC blog:
What should I do if I've paid? You should contact your bank and your local authorities, such as the police. If you paid with a credit card, your bank may be able to block the transaction and return your money. The following government-initiated fraud and scam reporting websites may also help:
If your country or region isn't listed here, we encourage you to contact your country's federal police or communications authority. For general information on what to do if you have paid, see:
How did message know my IP address? Your IP address is not usually hidden, and there are lots of tools online that will get it for you. It's likely they used such a tool. How did ransomware get on my PC? In most instances ransomware is automatically downloaded when you visit a malicious website or a website that's been hacked. For other ways malware, including ransomware, gets on your PC, see:
How do I protect myself against ransomware? You should:
You can backup your files with a cloud storage service that keeps a history or archive of your files, such as OneDrive which is now fully integrated into Windows 10 and Windows 8.1, and Microsoft Office. After you've removed the ransomware infection from your computer, you can restore previous, unencrypted versions of your Office files using 'version history'. See the question 'How do I get my files back?' above for more help on how to use this feature in OneDrive. For more tips on preventing malware infections, including ransomware infections, see:
How do I remove ransomware from my PC? How to remove the ransomware depends on what type it is. If your web browser is locked You can try to unlock your browser by using Task Manager to stop the web browser's process:
When you open your web browser again, you may be asked to restore your session. Do not restore your session or you may end up loading the ransomware again. See the question 'How do I protect myself from ransomware' above for tips on preventing browser-based ransomware from running on your PC. If your PC is locked Method 1: Use the Microsoft Safety Scanner in safe mode First, download a copy of the Microsoft Safety Scanner from a clean, non-infected PC. Copy the downloaded file to a blank USB drive or CD, and then insert it into the infected PC. Try to restart your PC in safe mode:
When you're in safe mode, try to run the Microsoft Safety Scanner. Method 2: Use Windows Defender Offline Because ransomware can lock you out of your PC, you might not be able to download or run the Microsoft Safety Scanner. If that happens, you will need to use the free tool Windows Defender Offline:
See our advanced troubleshooting page for more help. Steps you can take after your PC has been cleaned Make sure your PC is protected with antimalware software. Microsoft has free security software that you can use:
If you don't want to use Windows Defender or Microsoft Security Essentials, you can download other security software from another company. Just make sure it is turned on all the time, fully updated, and provides real-time protection. |
Microsoft Technical Security Notifications Excerpted from: https://technet.microsoft.com/en-us/security/dd252948 Help protect your computing environment by keeping up to date on Microsoft technical security notifications. Security Update Email Alerts Microsoft's free monthly Security Notification Service provides links to security-related software updates and notification of re-released security updates. You can choose between basic and comprehensive formats.These notifications are written for IT professionals, contain in-depth technical information, and are digitally-signed with PGP.
Security Advisories Alerts Microsoft Security Advisories are a way for Microsoft to communicate security information to customers about issues that may not be classified as vulnerabilities and may not require a security bulletin. Each advisory will be accompanied with a unique Microsoft Knowledge Base Article number for reference to provide additional information about the changes.
Microsoft Security Response Center Blog Alerts The Microsoft Security Response Center (MSRC) blog provides a real-time way for the MSRC to communicate with customers. You can also follow us on our Twitter feed @msftsecresponse.
Help with Your Notification Services If you have any problems registering, canceling, or receiving the security notifications, please contact us. To set your contact preferences for this and other Microsoft communications, see the communications preferences section of the Microsoft Privacy Statement at: < http://go.microsoft.com/fwlink/?LinkId=92781>.
Pretty Good Privacy (PGP) is an Internet standard for digitally signing and encrypting e-mail and other documents. The Microsoft Security Response Center (MSRC) uses PGP to digitally sign all security notifications. However, it is not required to read security notifications, read security update information, or install security updates. You can obtain the MSRC public PGP key at the MSRC Security Notification PGP Web page. Numerous third-party vendors produce PGP-compatible applications for a variety of platforms, but Microsoft cannot recommend the right solution for your environment. |
Anshuman Mansingh Technology Solutions Professional https://www.linkedin.com/in/anshumanmansingh |